Challenge
The M-21-31 Memorandum is a critical initiative to enhance the visibility of cybersecurity events generated by federal Information Technology (IT) and Internet of Things (IoT) assets. It impacts all federal agencies and executive departments.
When properly analyzed, this data helps detect patterns and trends that improve government visibility before, during, and after cybersecurity incidents. This visibility empowers organizations to plan effectively, act decisively, and strengthen their security posture while optimizing investigative and remediation capabilities.
Capturing millions of daily events and storing them for efficient retrieval, however, is costly. Since compliance with most Executive Orders is not optional and additional funding is limited, agencies face a formidable challenge.
Building on Executive Order 14028 and the updated National Cybersecurity Strategy, M-21-31 outlines the logging, retention, and management requirements needed for Security Operations Centers (SOCs) to reach the highest maturity level (EL3). Achieving this requires a logging strategy that incorporates all sources, additional compute, and expanded storage.
Challenges organizations face include:
- Generating terabytes of logs daily
- Rising Cloud Service Provider fees (compute, transit, storage)
- Complex SIEM implementations creating vendor lock-in
- Increasing OpEx and CapEx costs
- Difficulty recalling and searching logs effectively
- SIEM licensing fees scaling with organizational growth
Critical M-21-31 Compliance Questions:
- How do federal organizations find a compliant, cost-effective solution that evolves with changing requirements?
- How can agencies retain 12 months of active logs and petabytes of PCAP while keeping costs under control?
- How can they implement a strategy that scales with mission dynamics, attack variations, and investigative needs?
Solution
Koniag Government Services, LLC (KGS) has created and successfully deployed a solution that met the M-21-31 requirements, placing our customer in the top 2% of all federal Agencies and saving 1.6 million dollars annually. KGS has developed a log collection and vendor-neutral SIEM architecture that cost-effectively addresses M-21-31 requirements. It resolves the ingest and storage challenges while focusing the SIEM on practical security operations use cases and just-in-time analysis for investigations. The following figure depicts a high-level architecture that decouples data ingested from proprietary vendor solutions.
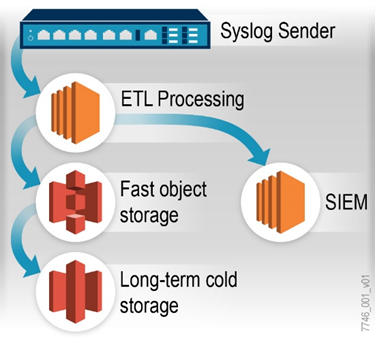
KGS’ Extract, Transform, and Load (ETL) operations strategy solves the problems surrounding the need for multiple vendors, the ever-changing standards across those vendors, and making successful log correlations across multiple formats. An ETL function (or pipeline) takes raw information and applies formatting and other logic to ensure the data loaded into the data lake has been homogenized. The KGS M-21-31 solution leverages the scale and flexibility of the Amazon Web Services (AWS) cloud to handle real-time processing of logs, metrics, traces, and IT and security-relevant data efficiently and cost-effectively. This solution allows our customers to log 200,000 events per second from over 500 unique source types across 20,000 devices and over 70 cloud service providers. By leveraging cloud Infrastructure as a Service scaling and flexibility along with an object storage data lake.
Before M-21-31 was issued, our Government customer spent $1.5M a year in SIEM licensing and AWS costs to meet their security operations and investigative requirements. The agency projected an annual increase of $4.8M to meet the new requirements. The KGS team worked with the technology providers and agency to deliver a solution that met all the new requirements for $3.2M a year, saving our Government client $1.6M a year in SIEM licensing, computing, and storage costs. Additionally, our solution decoupled the SIEM from the data lake. This eliminated the vendor lock-in the agency was experiencing with their SIEM vendor, allowing them to change software providers if desired.
Before introducing the KGS M-21-31 solution, the mean time to restore archived SIEM data from cold storage, data greater than 90 days in age, would take over 45 days in addition to $145,000 in cloud egress and infrastructure costs. This limitation was based on slow storage techniques that saved the Agency money by leveraging slower-performance data storage. The KGS solution eliminated this restriction, cutting the restoration time for archived data to minutes.
Another issue the Agency was experiencing with the previous SIEM solution was using regex and scripts as part of the ETL process to homogenize the logging data. This was complex and required programming efforts to address changes whenever any of the 500+ source-type vendors changed log information, which happened more often than was anticipated. The result exposed visibility gaps in the security posture due to a backlog of vendor-driven ETL changes required to keep the system functioning. The KGS M-21-31 solution introduced a modern ETL process and eliminated this complexity, thus preventing a backlog from being created.
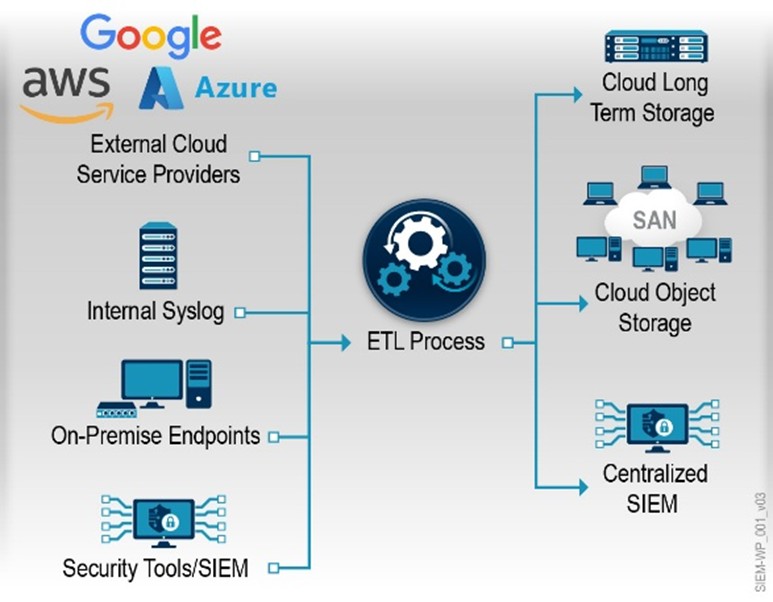
The introduction of a modern ETL process also allowed the Agency to, as noted in M-21-31, “provide, upon request and to the extent consistent with applicable law, relevant logs to the Cybersecurity and Infrastructure Security Agency (CISA) and Federal Bureau of Investigation (FBI).” This is possible because the Agency can keep one year of logs in a rapidly accessible format while ensuring the information required to support security operations is in the SIEM for immediate analysis.
Other benefits the KGS M-21-31 solution provides our customer are:
- Provided capability to retrieve data from any source at any time, including SIEM tools such as Arcsight, Syslog, and Splunk
- Created a cloud-based object storage data lake with an easy life cycle policy for long-term storage across any cloud provider, and centralized the data with the necessary correlations
- Centralized the agency SIEM, while creating the flexibility to leave legacy logging systems in place until cutover is ready
- Established ability to replay data from Cloud Object Storage to SIEM to support investigations, sending only relevant data while reducing costs
- Implemented an object storage data lake with one year of logging, which is drastically cheaper than provisioning local or server-attached storage on-premise or through IAAS
- Future-proofed the design by storing data in the data lake in a homogenized format
Conclusion
Identifying behavior patterns by monitoring dashboards and alerts from thousands of systems, network devices, applications, host intrusion systems, threat intelligence sources, and phishing alerts is a complex problem SIEM providers are eager to help agencies solve. M-21-31 represents a significant increase in logging volume, which translates to higher SIEM licensing costs and increased infrastructure expenses. New techniques are required to manage costs and increase the functionality of the SIEM so the visibility required by M-21-31 can be realized. M-21-31 allows agencies to realize goals outlined in Executive Order 14028 by harvesting all required logs and shared amongst federal agencies.
Monitoring threats for all the devices and behavior on a network at scale is challenging. Investigating incidents in a reasonable amount of time is critical, and the agency can not continue to take weeks to review petabytes of information when the technology exists to reduce it to minutes, reduce overhead costs, and prevent vendor lock-in. KGS’ solution shows how it is possible to meet M-21-31 requirements cost-effectively, deal with the dynamic nature of enterprise IT environments, and have the performance required to accomplish the mission and protect an organization.
Acquisition Strategy
KGS and its 28 subsidiaries are ideally suited as the prime contractor to receive a Small Business Administration (SBA) 8(a) directed award following Federal Acquisition Regulation (FAR) 19.804 and 13 Code of Federal Regulations (CFR) 124.503. As an Alaska Native Corporation (ANC) owned business, KGS provides the Federal Agencies with comprehensive capabilities and capacity that includes access to a deep portfolio of technical abilities, personnel, and experience from 2,600+ staff supporting 550+ contracts/tasks spanning technology, consulting, and operations support for defense, national security, health, and civilian agencies.
KGS provides a wide array of technology-focused services, including:
- Software engineering and development
- Artificial Intelligence (AI)/Machine Learning (ML)
- DevSecOps
- Enterprise infrastructure operations
- System and database administration
- System engineering
- Data management
- Cybersecurity
- Cloud modernization
- Intelligence analysis
- Risk management
- Business transformation
- Program management
- Cybersecurity operations
We deliver these services to multiple Government agencies, enabling national security, intelligence, and law enforcement missions. Our processes and service delivery approach uses industry best practices from Capability Maturity Model Integration (CMMI), International Organization for Standardization (ISO) 9001:2015 Quality Management, ISO/IEC 20000-1:2018 IT Services Management, ISO/IEC 27001:2022 Information Security Management, Information Technology Infrastructure Library (ITIL), and the Scaled Agile Framework (SAFe) methodologies that have been integrated into our tools and templates. KGS is appraised at CMMI Maturity Level 3 at the corporate level, reinforcing our robust processes, disciplined execution, and commitment to quality delivery support.
Learn More
If you found this white paper helpful and would like more information, please contact KGSinfo@koniag-gs.com. In your email, be sure to reference the white paper and include any specific follow-up requests or details you’d like us to provide.
